Security
Trustwave
Trustwave is the leading provider of on-demand data security and payment card industry compliance management solutions to businesses and organizations throughout the world. Trustwave has helped thousands of organizations — ranging from Fortune 500 businesses and large financial institutions to small and medium-sized retailers—manage compliance and secure their network infrastructure, data communications and critical information assets.
Network Security
- Trustwave Unified Threat Management (UTM) is the industry-leading solution that features unique, integrated security technologies that provide comprehensive protection for your network–all consolidated in a single appliance and delivered as a managed service.
Complexity – Managed
Organizations continue to be challenged with the growing complexity of the threat landscape and managing multiple security control technologies. Trustwave helps alleviate these challenges with complete management oversight.
Simple, Predictable Cost
All services provided by Trustwave’s Managed UTM roll-up to a single, monthly subscription fee. No separate or hidden license or maintenance fees and no capital expenses are incurred with our competitively-priced offering.
Fully owned Technology – No “Outsourcing”
All UTM technologies are fully owned and integrated by Trustwave, including services such as internal vulnerability scanning and network access control not typically found in UTM offerings. We do not “outsource” any portion of our service, providing a single point of accountability with better integration and faster response. - Intrusion Detection System
The goal of an Intrusion Detection System (IDS) is to monitor the effectiveness of control systems by monitoring for evidence of attacks. An intrusion detection system is often necessary to help control the risks associated with common vulnerabilities such as e-mail borne viruses, infected laptops and human factors.
To be effective, an Intrusion Detection System solution requires disciplined processes and expert staff, as well as a carefully configured and tuned monitoring configuration. That’s why so many organizations choose to outsource this vital service to Trustwave.
Trustwave’s Managed Intrusion Detection service is the cost-effective way to continuously monitor the security of your Internet and network infrastructure. The service monitors your network for the most severe exploits including worms, viruses, buffer overflows and denial-of-service attacks.
Security expertise
Unlike hardware or software oriented solutions, Trustwave’s Managed Intrusion Detection service relies on expert human analysis. This expertise helps distinguish potential threats from the many false-positives typically reported by automated IDS solutions.
Detailed reporting
Through Trustwave’s Security Console portal, you will have 24×7 online access to a range of valuable reports. To assist with internal control and compliance requirements, a record of all attack events and their subsequent analysis is automatically posted for your review and to support audit documentation requirements. - Intrusion Prevention System
Trustwave’s Intrusion Prevention System (IPS) is an asset-centric, easy-to-deploy and adaptive enforcement technology that works to complement your firewall perimeter. The Trustwave intrusion prevention system auto-tunes in real-time to address vulnerabilities specific to your network. This tailored approach strengthens your perimeter defenses while cutting down on false positives that can hinder legitimate traffic.
The Intrusion Prevention System has one simple goal: to interrupt any data flows that are identified as malicious before they can compromise your network.
Trustwave Intrusion Prevention = Extra Protection
Unlike other intrusion prevention systems, Trustwave’s IPS provides an easy-to-deploy appliance specifically configured for your network. This positioning ensures that protection takes effect before an attack reaches its intended target.
How our Intrusion Preventions System Works
Trustwave Intrusion Prevention System positions state-of-the-art technology at your network choke points to facilitate the examination of traffic passing through at the application layer. It then scans your network to identify assets and self-tunes to provide defense against only those attacks that threaten specific systems on your network.
Tustwave’s IPS integrates vulnerability identification and intrusion prevention into a single appliance.- Integrated Transparent Firewall — Enables your organization to control access inside the network to secure zones, with full-state inspection. The application-layer IPS shields assets against threats profiled via regular vulnerability scan assessments.
- Predictive Protection — We use a predictive protection model that applies a proactive, asset-centric approach. By profiling and dropping only those exploits that would otherwise succeed in compromising a vulnerable system, Trustwave’s IPS operates more effectively and efficiently.
- Adaptive Intelligence — Adaptive intelligence technology is the engine behind our predictive protection model. The Trustwave IPS automatically adapts its protective shield to match the specific risk profile of an organization’s network by self-tuning its intrusion prevention rules.
- Easy Deployment and Administration — Deploy easily, anywhere on an organization’s network — at the perimeter, the DMZ and/or on internal LAN segments — to create secure zones. As a transparent “Layer-2” bridging appliance, there are no IP address or routing changes. Your organization can easily protect assets without re-architecting the network.
- Reliable Performance — Trustwave’s IPS models are built using high quality hardware, including Intel processors and chipsets, Seagate hard drives and SuperMicro chasses.
- Network Access Control
Key Features of Trustwave’s Enterprise Network Access Control Solution- Integrates with Active Directory
- Works in any network infrastructure
- Match user identity to each device
- Zero-day threat protection
- Full protection for all endpoints
- Automated policy enforcements
- Analyze every packet from every device
- Analyze every packet from every device
- Unified view of end-point activity
Trustwave’s suite of integrated appliances is a scalable full-cycle Network Access Control solution designed to protect large enterprise networks. Trustwave offers full protection for all endpoints, managed and unmanaged, and works in any network infrastructure. Our solutions combine agent-less network access control with zero-day threat prevention and automated policy enforcement. Network intelligence provides a unified view of endpoint activity and delivers powerful analysis of your network’s history and usage. Together, these features deliver comprehensive endpoint control, offering security checks throughout the lifecycle of a device’s network access.
Trustwave management servers deliver centralized management and monitoring of Network Access Control appliances deployed throughout your enterprise. All devices and policies are managed from a central management consoles.
Application Security
Your Web applications are at the heart of your business – they hold your intellectual property, drive your sales, and keep the trust of your customers. But here’s the problem – they’re fast becoming the preferred attack vector of hackers.
And, with the persistent nature of today’s attacks, applications can easily be compromised when security is not considered and scoped into each phase of the software development life cycle – from design to development to testing and ongoing maintenance. When you take a holistic approach to your application security, you greatly enhance your ability to produce and manage stable, secure applications.
Web Application Firewall
Applications, including Web and mobile, are the foundation of business and collaboration.
In many cases, applications drive the entire operation of your business, and they’re accessing critical data continuously. That’s why applications are an increasingly high value target for hackers. In fact, in monitoring 200,000 websites, Trustwave SpiderLabs found that nearly 16,000 attacks occurred per day.
Ensuring security at the foundation of your software development and ongoing operations is critical to preventing attacks and keeping the hackers out of your applications. Adopting a holistic, life cycle approach can greatly enhance your ability to develop and manage stable, secure applications, and one of the critical elements of this life cycle approach is a Web application firewall (WAF).
Continuous Protection for Web Applications
Instantly detect and prevent threats and vulnerabilities to your applications and prevent sensitive data leaks. With built-in threat intelligence, a unique combination of positive and negative security, dynamic virtual patching, and an easy to install, easy to configure platform, Trustwave WebDefend delivers continuous protection for all your Web applications
- Threat Intelligence: The most complete negative security knowledge, gleaned from thousands of real-world engagements and continuous application threat research. Positive security is added with our dynamic profiling and learning engine.
- Real-Time Threat Detection and Blocking: With bi-directional traffic analysis, automated behavioral profiling and multiple collaborative detection engines, WebDefend can seek out abnormal behavior and improve threat blocking as well as prevent outbound data leaks.
- On-Demand Customization: Pre-define rules and customize scenarios to ensure that the protection of your application is immediate, and focused to your requirements.
- Versatile Deployment: Provides maximum protection and deployment versatility by accommodating inline or out-of-line installation.
- Intuitive and Interactive Interface: Easy-to-use management console provides a single point of configuration and monitoring, giving your administrators complete and immediate visibility and understanding of Web application architectures as well as security, without prior training.
- Built-in Compliance Reports: Facilitates compliance with PCI DSS requirement 6.6 and delivers pre-built and customizable reports that provide a view into your compliance posture as well as details on sensitive information use.
- Flexible Implementation: Available on premise as a turnkey appliance, or as a fully managed security service with 24×7 analysis from Trustwave’s team of MSS experts.
Web Content Monitoring
Trustwave’s WCM is a MasterCard qualified web-monitoring agent.
Offensive and illegal content on a company’s Web site can negatively impact your brand and your business. Trustwave’s Web Content Monitoring (WCM) solution can help you monitor online merchant activity, and allow you to take appropriate and timely action to address and resolve questionable content, to head off these threats to your business. Trustwave’s WCM is a MasterCard qualified web-monitoring agent.
An automated content monitoring solution that ensures regulatory, industry and proprietary standards, Trustwave’s WCM supports specific standards such as such as Visa’s e-commerce merchant inspection requirements and MasterCard’s BRAM program. WCM ensures your merchants are adhering to these regulations. Utilizing an automated scanning engine and a multi-tier workflow, Trustwave’s WCM detects, scans, inventories and analyzes Web site content, in a fraction of the time required to perform the same function manually. If a finding is identified, then a Trustwave Senior Analyst will conduct a real-time review and expedient reporting back to the client.
web content monitoring
A range of businesses have enlisted Trustwave to provide Web content monitoring, including acquiring banks, their merchants and many others. Trustwave maintains ties to law enforcement and investigative agencies, putting us at the forefront of the latest in law enforcement computer forensics and Internet surveillance practices. Trustwave leverages this experience and information to adapt the WCM solution to address the latest issues in illegal, unethical and fraudulent practices online.
Data Security
Trustwave research uncovers 89% of attacks continue to target your customer records. With data as the lifeblood of all organizations, it’s no wonder securing intellectual property and meeting compliance requirements continue to be a challenge.
For every business challenged by increasingly complex threats, Trustwave’s award-winning data security solutions keep it simple so you can keep growing. With Trustwave Data Security offerings you gain total content protection and control throughout your entire enterprise – from the desktop to the network perimeter – and for your data at rest and in motion.
When you choose Trustwave to protect your data, you get superior quality and advanced expertise. Plus, you gain a unique advantage with an offering that is part of our unified security approach, which allows layered security products to share intelligence and events that uncover threats that single, point products miss.
Experience the Trustwave Data Security advantage:
- Simplified Protection – Trustwave solutions deliver superior usability and automation to simplify and streamline your data security process
- Ensure Compliance – quickly become compliant with regulations, such as, PCI, HIPAA, SOX, and others.
- Superior Security – Trustwave patented technology provides the most advanced detection and protection of your intellectual property
Content Security
Key Secure Web Gateway Features
- Most accurate malware protection
- Safe and productive Web 2.0 use
- Flexible deployment options
- Ensures compliance and minimizes data loss
- Detailed and customizable reporting
Trustwave Secure Web Gateway (formerly known as M86 Secure Web Gateway) offers the most accurate protection from next-generation threats and the most flexible deployment options in the industry – providing the same high level coverage to remote, mobile and on premise users.
What makes Trustwave Secure Web Gateway different? It offers true, zero-day protection for your organization with its patented technology that instantly analyzes the “intent” of the code and doesn’t simply reply on a simple comparison to a list of known, infected sites.
SWG enables safe, productive access to Web 2.0 while ensuring compliance, minimizing data loss and eliminating malware risks. Centralized policy control and a single interface make the solution easy to manage – whether deployed as a traditional appliance, virtual appliance, hybrid cloud or any combination of the three.
Secure Web Gateway is an integral component of Trustwave’s Mobile Security solution, which provides automated “Self-Sealing” network protection for BYOD and other mobile devices through the integration of multiple award winning Trustwave technologies. Learn More
Trustwave SWG’s granular social media control coupled with anti-malware protection let you embrace Web 2.0 without worrying about data leaks, productivity loss or malware infections.
Web Filtering
Trustwave Web Filtering and Reporting Suite Features
- Safe access to YouTube
- Extensive application control
- On premise mobile and tablet protection
- High scalability
- Regulatory and AUP compliance tools
The award-winning Trustwave Web Filtering and Reporting Suite (formerly known as M86 Web Filtering and Reporting Suite) helps you enforce your AUPs and easily comply with regulations. Known for its fast performance and multi-tiered administration capabilities, Trustwave Web Filtering sits outside the flow of network traffic to quickly and accurately filter millions of Web sites in 100+ categories—without impacting bandwidth or productivity.
With remote web filtering protection, your organization can use Tablet User Identification and Activity Monitoring to gain insight into the activity of all on premise tablet users, including iPad.
Works with YouTube and other video filters to ensure your K-12 students have a safe, online environment for finding, organizing and sharing educational videos.
Email Gateway
Key Secure Email Gateway Features
- Protection from email-based, blended threats
- Prevents data loss
- Improves productivity by reducing employee spam management
- Ensures compliance with regulations and AUPs
Comprehensive reports provide your executives with the visibility into trends and help demonstrate ROI. Detailed reports allow you to monitor usage for security breaches and unproductive behavior.
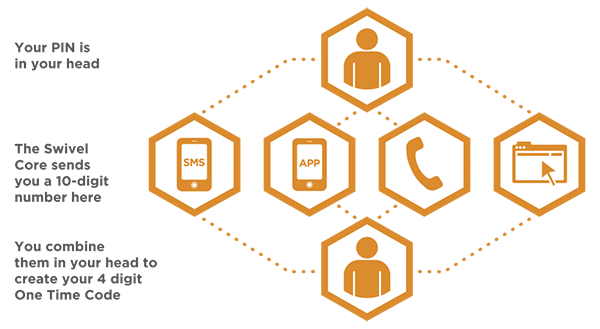
PINsafe
PINsafe is an authentication solution guarantees users a secure access to networks and computers without additional hardware (e.g. tokens). Using secure network connections (VPN), websites, corporate applications and/or mobile devices PINsafe assure a secure access after a successful authentication procedure.
- PINsafe is applied to ensure only full authenticated users, legitimated for a special security area, access to informations.
- Based on a unique combination of registered PIN-numbers and randomly generated security codes, sent to the users in an optimal way, PINsafe is one of the most secured, simple to use, reliable and economic authentication solutions in the whole market.
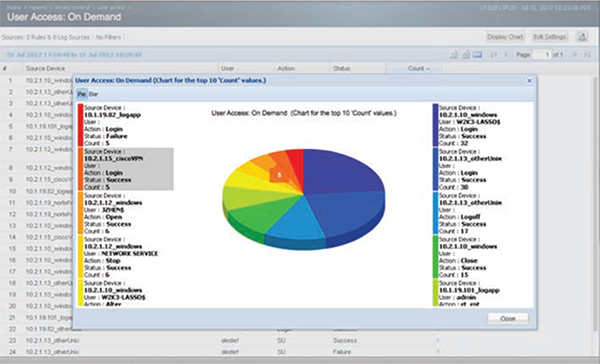
Tibco LogLogic
- Log Management
- Compliance Management
- Security Event Management
- Database Security Management
LogLogic offers a comprehensive suite of log management and security management products to help you:
- Achieve regulatory compliance
- Protect valuable company and customer information
- Improve the efficiency of your IT operations